JetStream DR for AVS can be configured to use Microsoft Entra ID for enhanced authentication with Azure storage accounts. This requires JetStream DR to be registered in Microsoft Entra ID as an application. The Microsoft Entra ID Application ID and Secret Key are used to access the storage account instead of an Access Key. Once JetStream DR has been registered in Microsoft Entra ID, the Azure storage account will be configured to grant JetStream DR virtual appliances access to the Blob storage with the required role.
The following items are required to configure JetStream DR for Microsoft Entra ID authentication:
- Microsoft Entra ID Tenant ID (Identifies the Microsoft Entra ID directory to use for authentication)
- Application ID (Uniquely identifies the JetStream DR application)
- Application Secret Value (Authenticates JetStream DR to Microsoft Entra ID)
Register JetStream DR as an Azure Application
- Sign into the Azure portal.
- Search for and select App registrations.
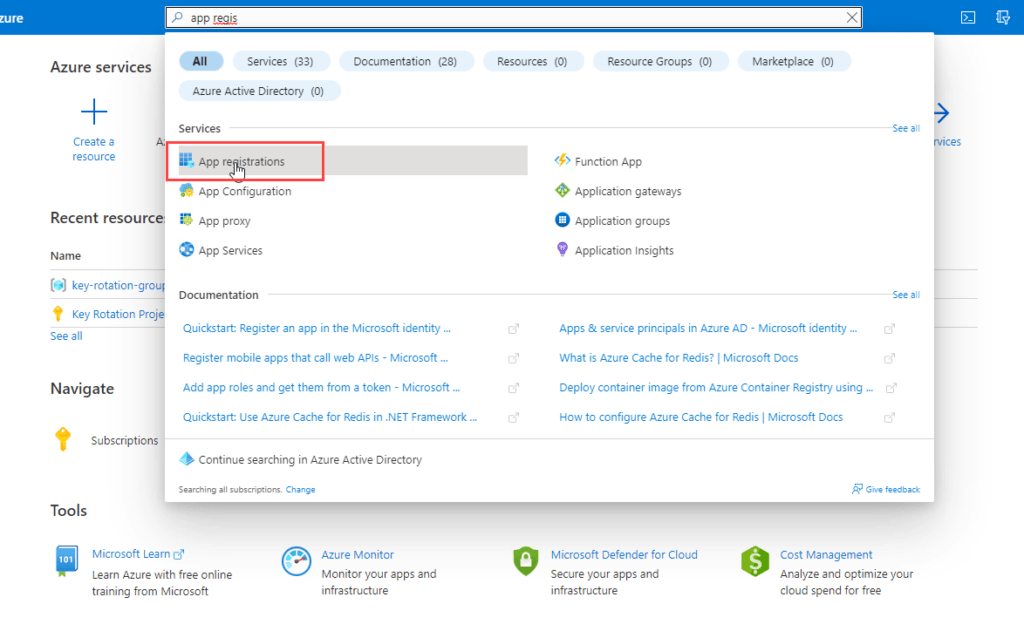
- Under Manage, select App registrations > New registration.
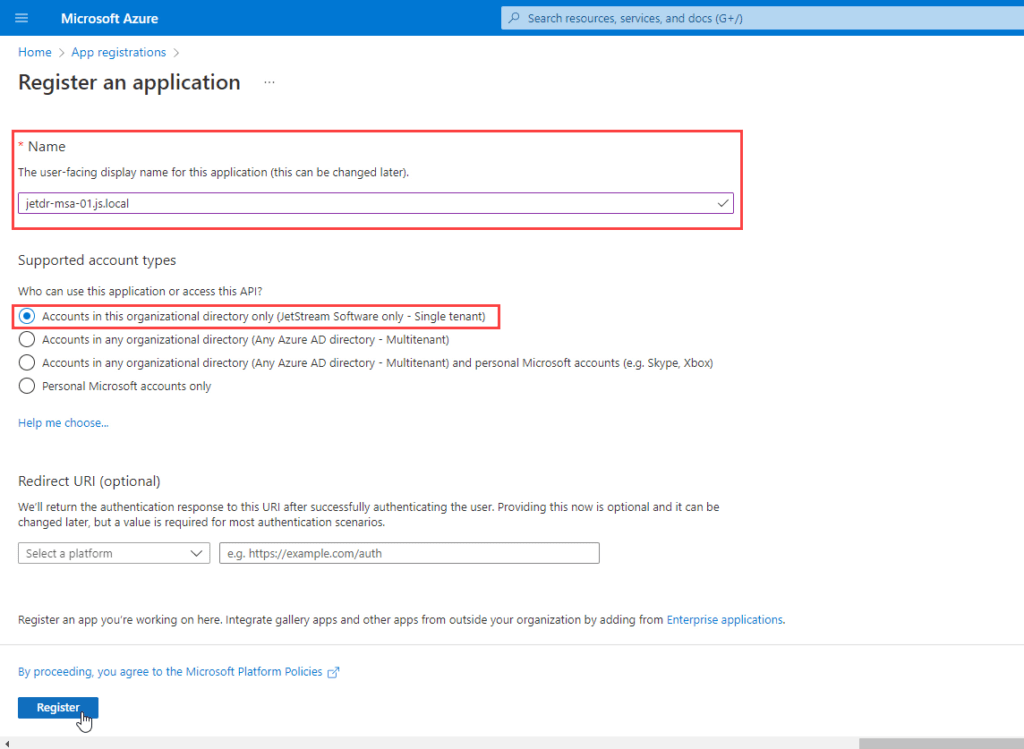
- Enter the JetStream DR MSA name as the display Name for your application. The display name will be used later to assign the application a role for the Azure Storage Account.
- Specify who can use the application. Select Accounts in this organizational directory only.
- Click Register to complete the initial app registration.
- When registration finishes, the Azure portal displays the app registration’s Overview pane. Record the Application (client) ID. This uniquely identifies the JetStream DR application, and the information will be used later to configure JetStream DR.
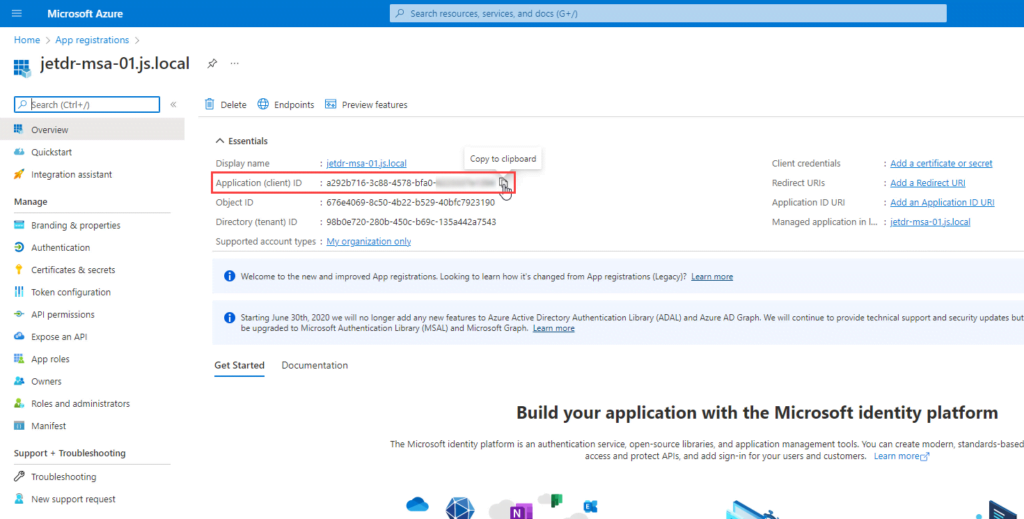
Create a Client Secret for the Registered Application
- Under Manage, select Certificates & secrets > Client secrets > New client secret.
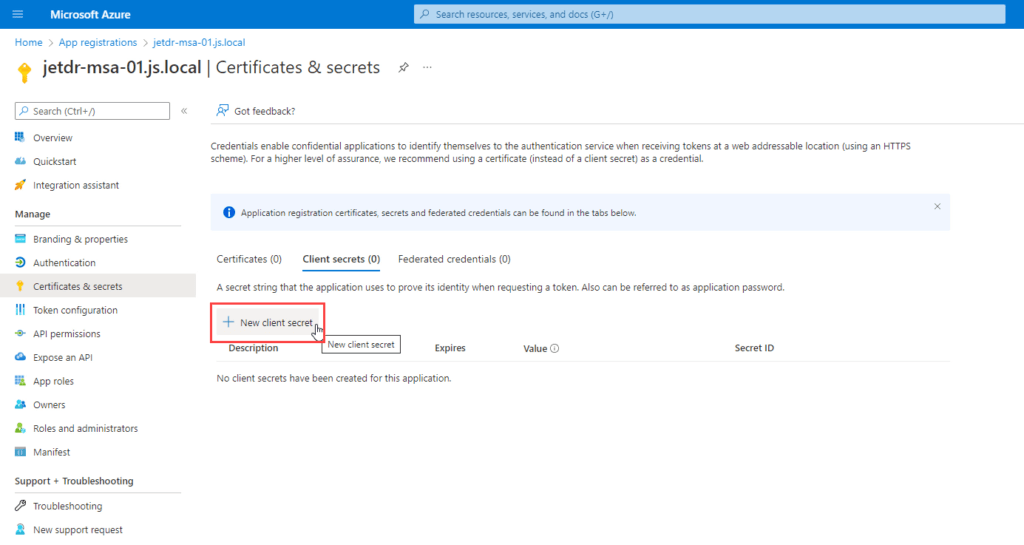
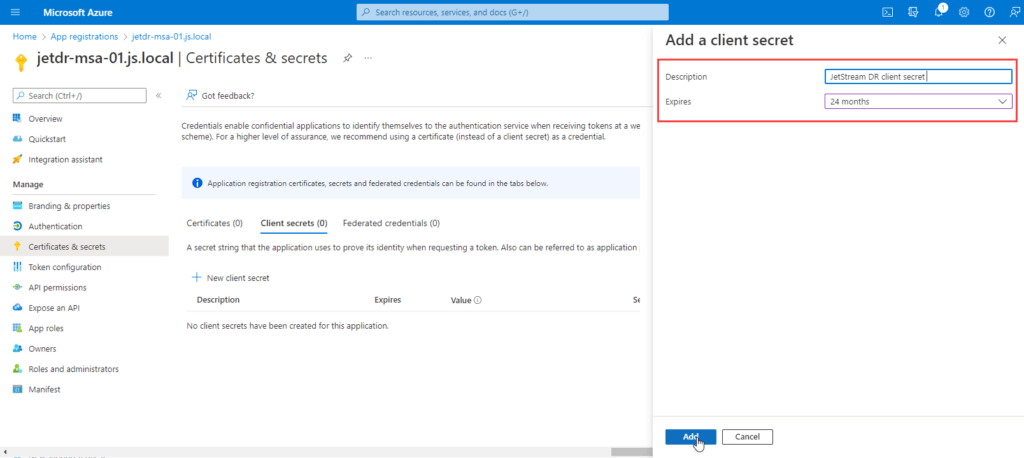
- Add a description for the client secret, then click Add.
- Select an expiration for the secret or specify a custom lifetime.
- Client secret lifetime is limited to two years (24 months) or less. You cannot specify a custom lifetime longer than 24 months.
- Microsoft recommends setting an expiration value of less than 12 months.
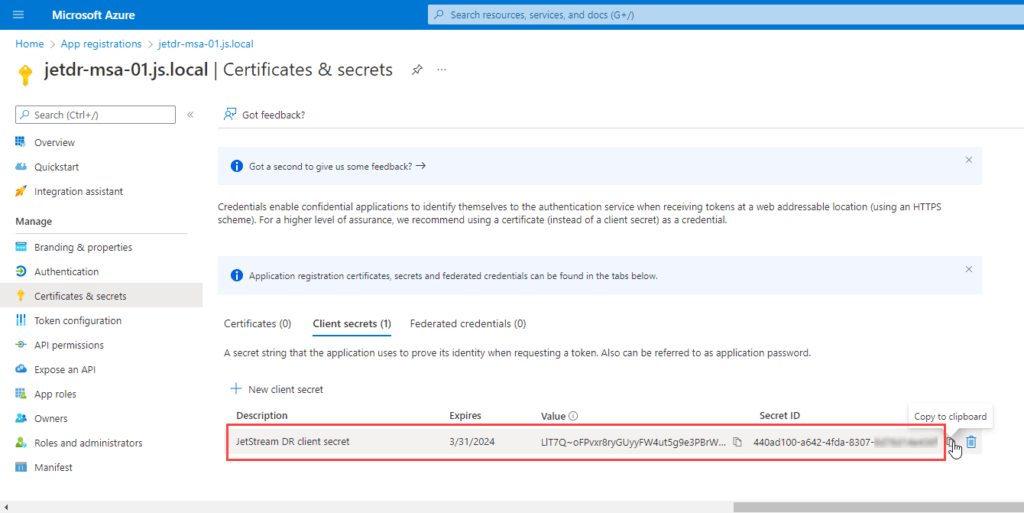
- Record the client secret value to use in the client application code.
- Important: The secret value will never be displayed again after you leave the page.
- This information will be used later to configure JetStream DR.
NOTE: Perform all the above steps for each site accessing Azure Blob Storage.
Configure an Azure Storage Account
- Go to the storage account.
- Click Access control (IAM).
- Click the Role assignments tab.
- Add a new role assignment.
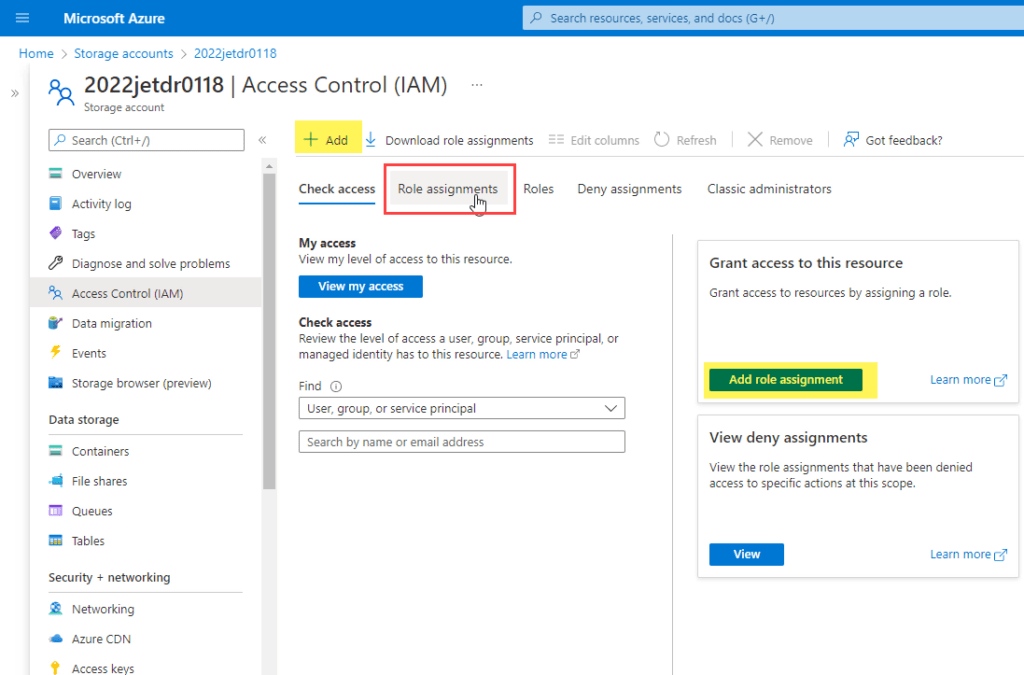
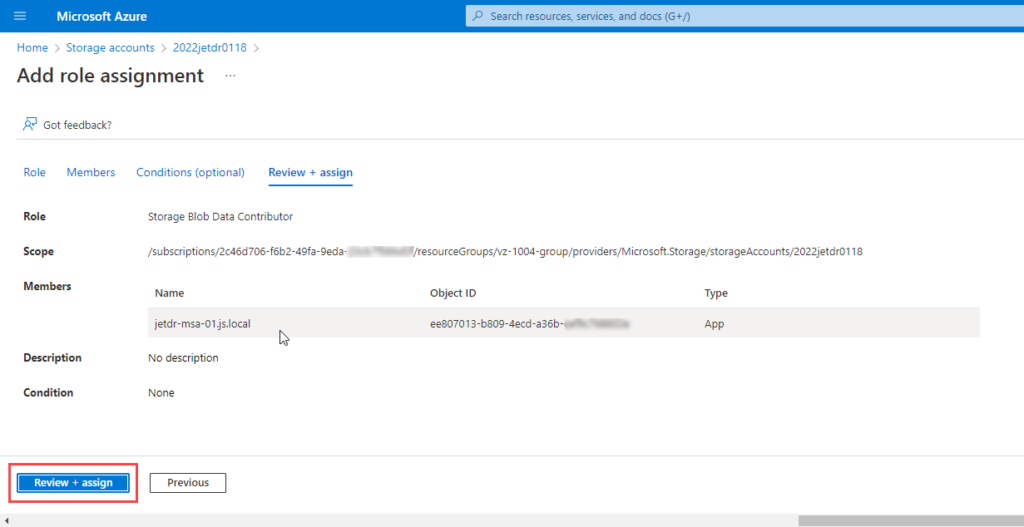
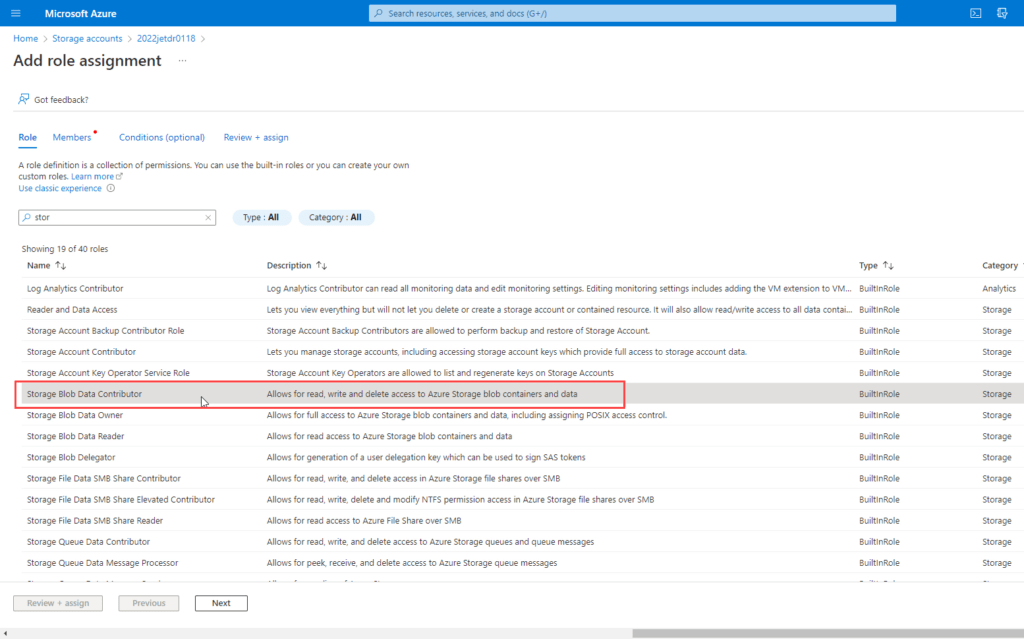
- On the role tab, select Storage Blob Data Contributor.
- Click Next.
- On the Members tab, assign access to: User, group, or service principal.
- Click +Select members.
- Begin typing in the Select box to search the directory for the registered application’s display name (configured previously).
- Click Select to add the application to the members list.
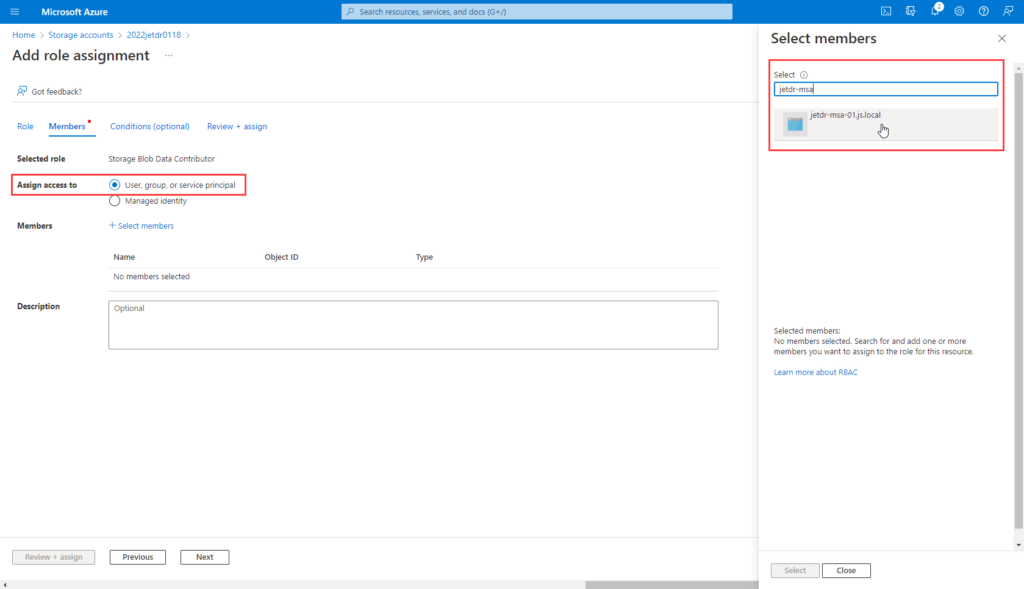
- Review the role assignment for the member.
- Click Review + assign.